Zero-Day Vulnerability Exploits
- By ThreatMatrix
In cybersecurity, the term zero-day vulnerability exploit describes a high-risk threat where attackers use unknown or unpatched software vulnerabilities to breach systems. These exploits pose significant risks for individuals and businesses alike, emphasizing the need for proactive measures to mitigate potential damages. In this article, we’ll explore what zero-day exploits are, why they’re so dangerous, and how organizations can defend against them.
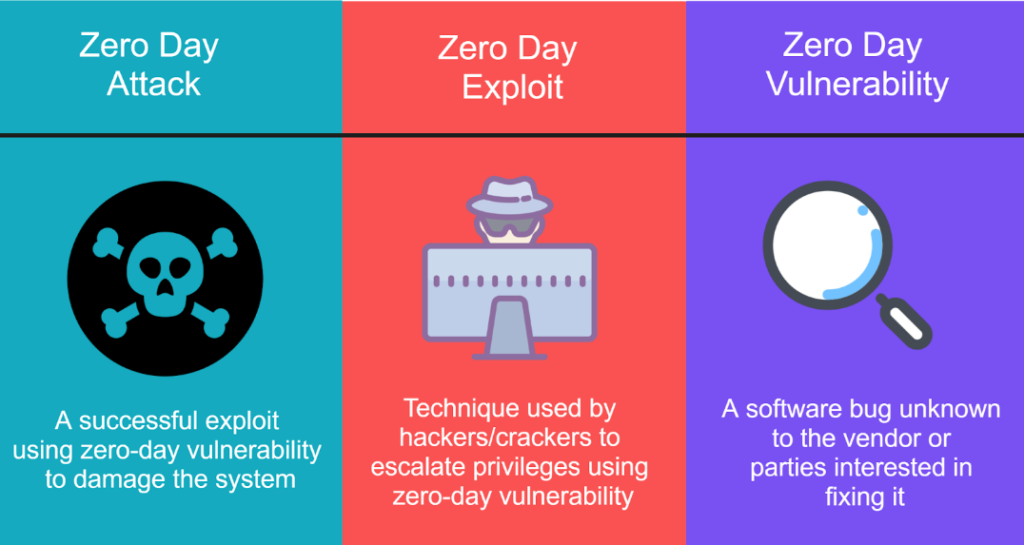
What Is a Zero-Day Vulnerability?
A zero-day vulnerability is a security flaw in software, hardware, or firmware that remains unknown to the vendor or has yet to be patched. The term “zero-day” signifies that the developers have had zero days to fix the vulnerability before it’s exploited. Cybercriminals use these flaws to execute malicious activities, from stealing sensitive data to launching ransomware attacks.
Why Zero-Day Vulnerabilities Are Dangerous
Since zero-day vulnerabilities are unknown to the software developers, there is no defense available at the time of attack. This makes them extremely valuable to hackers, who can exploit these weaknesses before a patch or fix is released. Furthermore, zero-day attacks are difficult to detect due to the lack of predefined signatures or patterns that security systems rely on for identification.
How Zero-Day Vulnerability Exploits Work
Exploiting a zero-day vulnerability often involves:
- Discovery of the Flaw: Hackers find or purchase details of an unknown vulnerability in popular software applications or operating systems.
- Developing an Exploit: Attackers create malicious code or tools that can exploit the identified flaw.
- Launching the Attack: Once the exploit is ready, attackers deploy it through phishing emails, infected files, or malicious websites.
High-Profile Examples of Zero-Day Exploits
Several notorious incidents highlight the damage caused by zero-day vulnerability exploits. One prominent example is the Stuxnet worm, which exploited multiple zero-day vulnerabilities to disrupt Iran’s nuclear facilities. More recently, the Log4Shell exploit targeted the widely-used Log4j library, affecting millions of systems worldwide before a fix was deployed.
Common Targets for Zero-Day Exploits
Zero-day exploits often target widely-used software and platforms, such as:
- Operating Systems (e.g., Windows, Linux, macOS)
- Web Browsers (e.g., Chrome, Firefox, Safari)
- Popular Applications (e.g., Microsoft Office, Adobe Acrobat)
Such applications are commonly targeted because they are widely deployed, providing a larger pool of potential victims.
Detecting Zero-Day Vulnerability Exploits
Challenges in Detection
Identifying zero-day attacks is challenging because traditional security measures rely on known threat signatures. To detect zero-day vulnerabilities, organizations often use advanced techniques, such as anomaly detection, which looks for unusual behavior or deviations from regular network traffic.
Advanced Detection Tools
Emerging tools, including machine learning algorithms, behavioral analysis, and threat intelligence platforms, are enhancing zero-day detection capabilities. By recognizing patterns and anomalies in system activity, these tools can flag potential zero-day vulnerabilities before they lead to a large-scale breach.
Protecting Against Zero-Day Vulnerability Exploits
Best Practices for Organizations
- Regular Software Updates: Keep software and systems updated with the latest patches to reduce vulnerability exposure.
- Threat Intelligence Feeds: Subscribe to threat intelligence feeds to stay informed about potential zero-day vulnerabilities.
- Network Segmentation: By segmenting critical parts of your network, you limit the spread of any breach caused by a zero-day exploit.
- Employee Training: Educate staff on recognizing phishing scams and other social engineering tactics that commonly deliver zero-day payloads.
Role of Advanced Security Solutions
Investing in advanced security solutions, such as Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) systems, can improve protection against zero-day exploits. These tools monitor endpoints and the network for unusual activity, offering a faster response to potential threats.
Importance of Zero-Day Vulnerability Management
With zero-day attacks increasing, proactive management is essential to protect data and maintain cybersecurity resilience. By prioritizing security updates, employee training, and robust threat monitoring, organizations can mitigate the risk of zero-day vulnerability exploits and protect their systems from unforeseen attacks.
Additional Resources on Zero-Day Security
For more insights on managing zero-day vulnerabilities and protecting against exploits, consider these resources:
- NIST Cybersecurity Framework – Guidelines for improving critical infrastructure security.
- MITRE ATT&CK Framework – A knowledge base of adversarial tactics and techniques to enhance threat detection capabilities.
